HR Organizational Chart - Change Control and QA

USJMX AWS Architecture

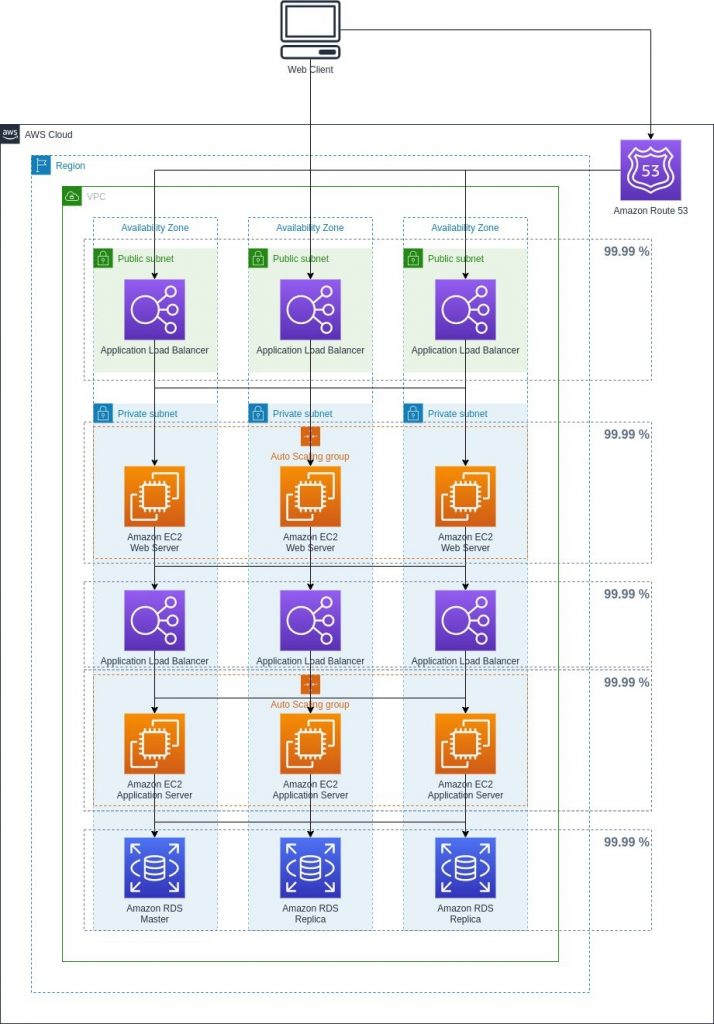
USJMX Amazon Architecture
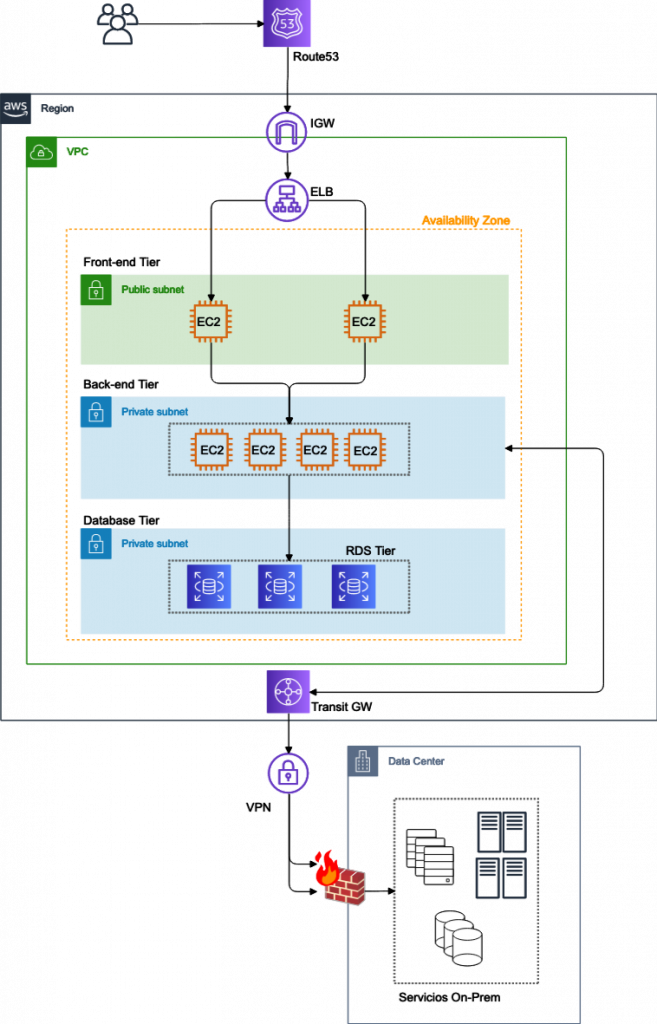
Business Continuity on AWS: Availability and Resiliency
USJMX AWS Security
AWS USJMX VPS is a secure and durable technology platform with industry-recognized certifications and audits: PCI DSS level 1, ISO 27001, FISMA Moderate, FedRAMP, HIPAA and SOC 1 (previously known as SAS 70 and/or SSAE 16) and SOC 2 audit reports. Our services and data centers have multiple layers of operational and physical security to ensure the integrity and security of your data.

USJMX AWS Datacenters
The USJMX AWS Cloud operates 35 availability zones in 13 geographic regions around the world and 4 more online regions. The UpTime of the datacenters are 99.95% Tier III+ category according to UpTime Institute.

USJMX Amazon VPS Features

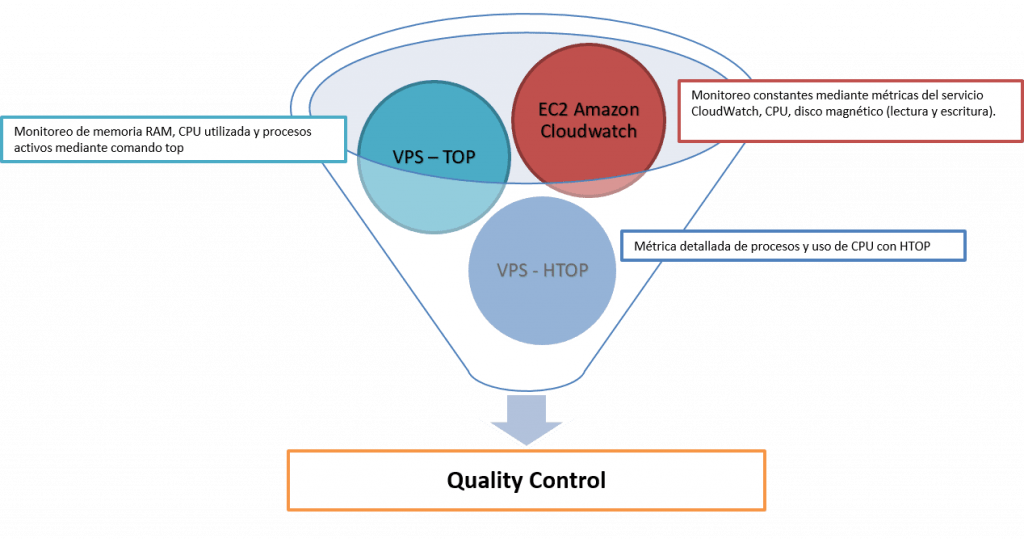
USJMX Monitoring
These metrics show the current performance of the equipment, so it is even possible to compare a 2-week old equipment.
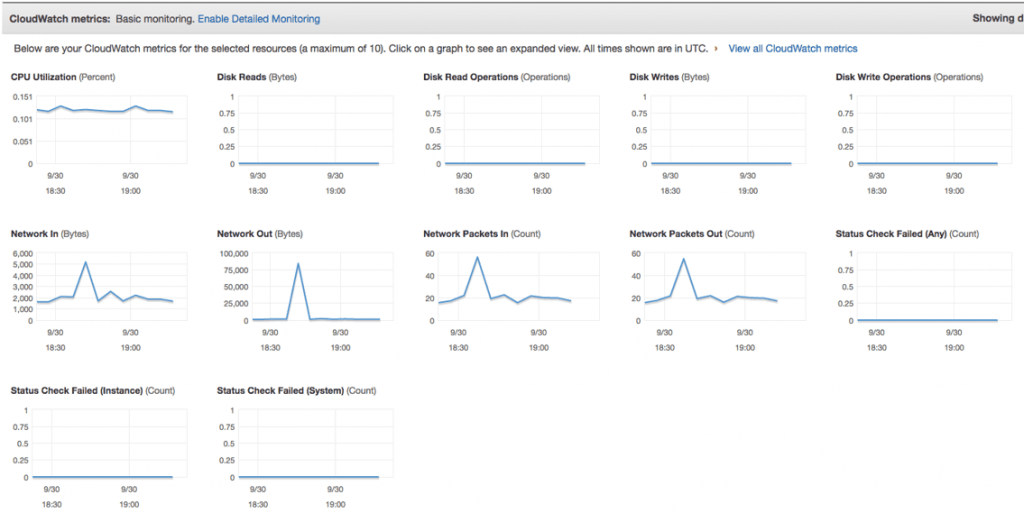
USJMX Stress test performed
Stress on USJMX systems and their performance
USJMX Security via WS
Given the characteristics of our systems and implementations, it is necessary to have a robust and secure methodology for the generation of connections via web services between the modules that make up our solutions and additionally externally with the services and Core systems of our customers.
For this specific purpose we have considered 2 frameworks that supply us with the main security features necessary for the implementation of our systems, beyond the encryption through SSL secure connections (HTTPS) and integration through VPN funnels, these frameworks are:
- Apache Shiro
- Oauth2 protocol in SpringBoot
Both tools can be deployed independently or in an architecture that mixes certain complementary features to arrive at an implementation that meets the security needs of the customer.
Apache Shiro
Apache Shiro Cryptography Features
Interface-driven, POJO based: all Shiro APIs are interface-based and implemented as POJO. This allows you to easily configure Shiro Cryptography components with JavaBeans compatible formats such as JSON, YAML, Spring XML and others. You can also override or customize Shiro as you see fit, leveraging its API to save you time and effort.
Simplified wrapper over JCE: Java Cryptography Extension (JCE) Shiro's cryptography APIs understand, use and simplify JCE concepts.
"Object Orientifies" cryptography concepts: Integration of JDK / JCE Cipher and Message Digest (Hash) classes. Shiro 'Object Orientify' Ciphers and Hashes, allows through a clean object hierarchy, implementation by simple instantiation.
Runtime Exceptions: Cryptographic exceptions are handled as runtime exceptions. You can decide whether or not to catch an exception according to your needs.
Default interface implementations: Shiro provides ready-to-use default Hash implementations (also known as Message Digests in the JDK), such as MD5, SHA1, SHA-256 and others.
Built-in Hex and Base64 conversion: Shiro Hash instances can automatically provide Hex and Base-64 encoding of hash data through its toHex () and toBase64 () methods.
Oauth2
Oauth2 protocol in SpringBoot
OAuth2 defines the following server-side roles:
- Resource owner: the service responsible for controlling access to resources.
- Resource server: the service that actually supplies the resources.
- Authorization server: the service management authorization process that acts as an intermediary between the client and the resource owner.
JSON Web Token, or JWT: is a specification for the representation of claims to be transferred between two parties. Claims are encoded as a JSON object that is used as the payload of an encrypted structure, allowing the claims to be digitally signed or encrypted.
The containing structure can be either JSON Web Signature (JWS) or JSON Web Encryption (JWE).
JWT can be chosen as the format for accessing and updating tokens used within the OAuth2 protocol.







